July 2015 Android malware review from Doctor Web
OREANDA-NEWS. In July, an entry for a rather interesting Trojan named Android.Poder.1 was added to Dr.Web virus database. This malicious program incorporated into various harmless applications (mostly games) can steal confidential data stored on the infected device, send SMS messages with a link to download the Trojan's copy to contacts from the victim's phone book, and display advertisements in the status bar. Moreover, Android.Poder.1 can generate income for its creators using another method—to access some application features, available free of charge in original versions, users are prompted to pay some amount of money that is subsequently forwarded to cybercriminals' account. The Trojan has the following characteristics:
- Incorporated in applications modified by cybercriminals
- Can gather confidential data, including browsing history and information on bookmarks
- Can send SMS messages with a link to download the Trojan's copy to contacts from the victim's phone book (depending on the application's modification, messages can be sent without victim's knowledge or with their consent—in that case, standard SMS message form is used)
- Has several program modules that serve the purpose of displaying annoying advertisements
- Can provide paid access to some features of the compromised application
Android Trojans on Google Play
During the previous month, Doctor Web security researchers detected a number of Android Trojans distributed through Google Play. These malicious programs named Android.Spy.134 and Android.Spy.135 were incorporated into harmless games and were able to display a fake Facebook authentication form prompting users to enter their login and password details into that form. The divulged data was forwarded to the remote server. Subsequently, users from the victim's contact list received a message from their “friend” advising them to download a modified version of a game. This scheme allowed cybercriminals to distribute their creations on a large scale—thus, Android.Spy.134 and Android.Spy.135 had already been downloaded from Google Play more than 500,000 times before they were removed from the website.
Distribution and features are as follows:
- More than 500,000 downloads on Google Play
- Created using Mono Framework
- Look and function like legitimate games
- Can display a fake Facebook authentication form prompting users to enter their login and password details
- Can send messages to victim's Facebook friends advising them to download a modified version of a game
At the end of July, Doctor Web security researchers detected yet another Trojan named Android.DownLoader.171.origin on Google Play. This malicious application is designed to download and install other programs on Android mobile devices. Moreover, upon receiving a command from cybercriminals, it can remove already installed software. In addition to that, Android.DownLoader.171.origin is able to display advertisements in the status bar.
Before this Trojan was detected on Google Play, it had already been downloaded by more than 100,000 users. However, cybercriminals also used other Internet resources (mostly oriented towards Chinese users) to distribute the malware. As a result, the total number of downloads exceeded 1.5 million. Find out more about Android.DownLoader.171.origin in the news article published by Doctor Web.
Backdoors
During the previous month, Dr.Web virus database was updated with a number of new entries for backdoors belonging to the Android.Backdoor family. Upon receiving a command from cybercriminals, these programs can preform a number of malicious actions on infected mobile devices. In particular, Android.Backdoor.114.origin and Android.Backdoor.213.origin were among the detected malware. These programs are incorporated into harmless applications and can steal confidential information and stealthily download and install other malware on the infected device. Moreover, Android.Backdoor.114.origin attempts to gain root access to ensure its installation in the system folder and protect itself from being removed.
The number of entries for Trojans of the Android.Backdoor family in Dr.Web virus database:
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| 214 | 257 | +20.1% |
Android ransomware
In July, a large number of ransomware Trojans belonging to the Android.Locker family were detected. These malicious programs lock mobile devices and demand a ransom to unlock them. During the previous month, Dr.Web virus database was updated with new entries for these Trojans.
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| 301 | 356 | +14.8% |
Banking Trojans
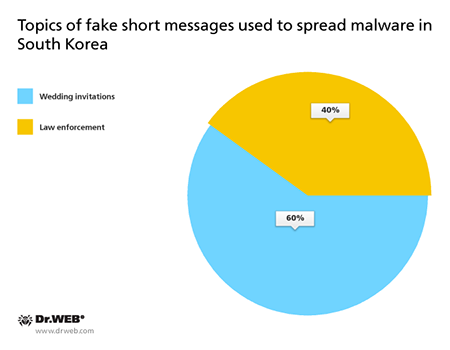
During the previous month, cybercriminals continued to distribute various Trojans designed to steal money from bank accounts of mobile devices' owners. For example, cybercriminals from South Korea organized several spam campaigns involving short messages with malware download links. In comparison with the previous month, the number of such attacks decreased significantly and included fewer than 10 incidents.
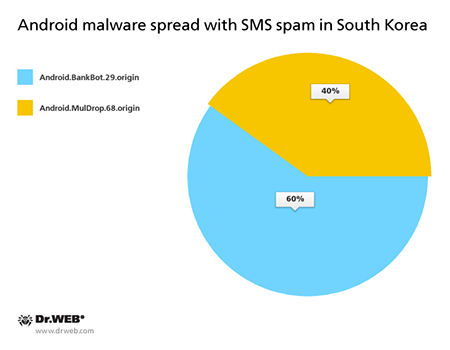
In July, the following malicious programs for Android were distributed in South Korea via SMS spam messages:
The number of entries for banking Trojans of the Android.BankBot family in Dr.Web virus database:
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| 122 | 135 | +10.65% |
-
Android.BankBot.29.origin
A banking Trojan that steals authentication information used by the clients of some South Korean financial organizations. Once a popular online banking application is launched, the Trojan replaces its interface with a fake one that prompts the user to enter all confidential data necessary to control their bank account. The divulged data is forwarded to cybercriminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
-
Android.MulDrop.68.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
SMS Trojans
Moreover, during the previous month, a large number of new SMS Trojans were detected. These malicious applications send messages to premium numbers and subscribe users to chargeable services without their victims' knowledge. The number of entries for SMS Trojans of the Android.SmsSend family in Dr.Web virus database:
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| 4,745 | 5,259 | +10.83% |





Комментарии