29.05.2015, 15:31
May 2015 Android malware review from Doctor Web
OREANDA-NEWS. May was marked by high activity of banking Trojans targeting users of Android devices and distributed by cybercriminals in a number of countries. For this purpose, virus makers extensively used unsolicited SMS messages containing a link to download one or another Trojan. For example, in Russia, cybercriminals used already known topics for their MMS messages. Among banking Trojans, spread by means of short messages, a number of Android malware belonging to the Android.SmsBot family were detected (in particular, Android.SmsBot.269.origin and Android.SmsBot.291.origin).
The number of entries for banking Trojans of the Android.BankBot family in Dr.Web virus database:
Android.SmsBot.269.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android.SmsBot.291.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android.BankBot.29.origin
A banking Trojan that steals authentication information used by the clients of some South Korean financial organizations. Once a popular online banking application is launched, the Trojan replaces its interface with a fake one that prompts the user to enter all confidential data necessary to control their bank account. The divulged data is forwarded to cybercriminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
Android.MulDrop.53.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
Android.MulDrop.65.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
Android.Banker.54.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
The number of entries for SMS Trojans of the Android.SmsSend family in Dr.Web virus database:
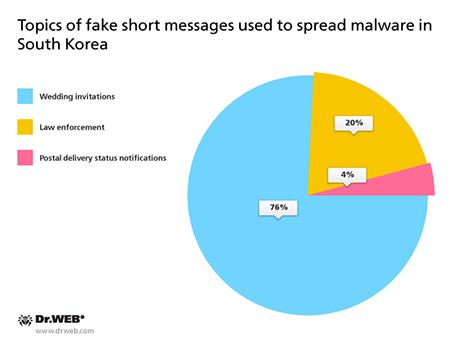
Again, a large number of attacks with the use of banking Trojans were registered is South Korea; that is, in May, Doctor Web security researchers detected more than 20 spam campaigns organized by cybercriminals. The following topics were used for the messages:
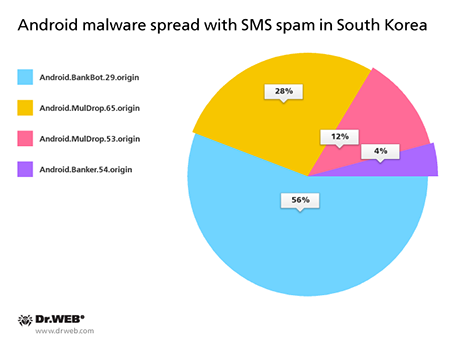
Malicious applications that performed the attacks
Moreover, during the previous month, new banking Trojans belonging to the Android.BankBot family came into view. Despite the fact that the virus makers responsible for the creation of these Trojans had been arrested in April, distribution of this malware continued by other cybercriminals.The number of entries for banking Trojans of the Android.BankBot family in Dr.Web virus database:
| April 2015 | May 2015 | Dynamics |
|---|---|---|
| 110 | 119 | +8.2% |
Android.SmsBot.269.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android.SmsBot.291.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android.BankBot.29.origin
A banking Trojan that steals authentication information used by the clients of some South Korean financial organizations. Once a popular online banking application is launched, the Trojan replaces its interface with a fake one that prompts the user to enter all confidential data necessary to control their bank account. The divulged data is forwarded to cybercriminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
Android.MulDrop.53.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
Android.MulDrop.65.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
Android.Banker.54.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android ransomware
May also experienced the discovery of new ransomware species of the Android.Locker family. These programs lock Android devices and demand a ransom to unlock them. The number of entries for these dangerous malicious applications in Dr.Web virus database:
| April 2015 | May 2015 | Dynamics |
|---|---|---|
| 227 | 266 | +17.2% |
SMS Trojans
During the previous month, Doctor Web security researchers detected a large number of new SMS Trojans belonging to the Android.SmsSend family and designed to send messages to premium numbers and subscribe users to chargeable services.The number of entries for SMS Trojans of the Android.SmsSend family in Dr.Web virus database:
| April 2015 | May 2015 | Dynamics |
|---|---|---|
| 3,900 | 4,204 | +7.8% |






Комментарии